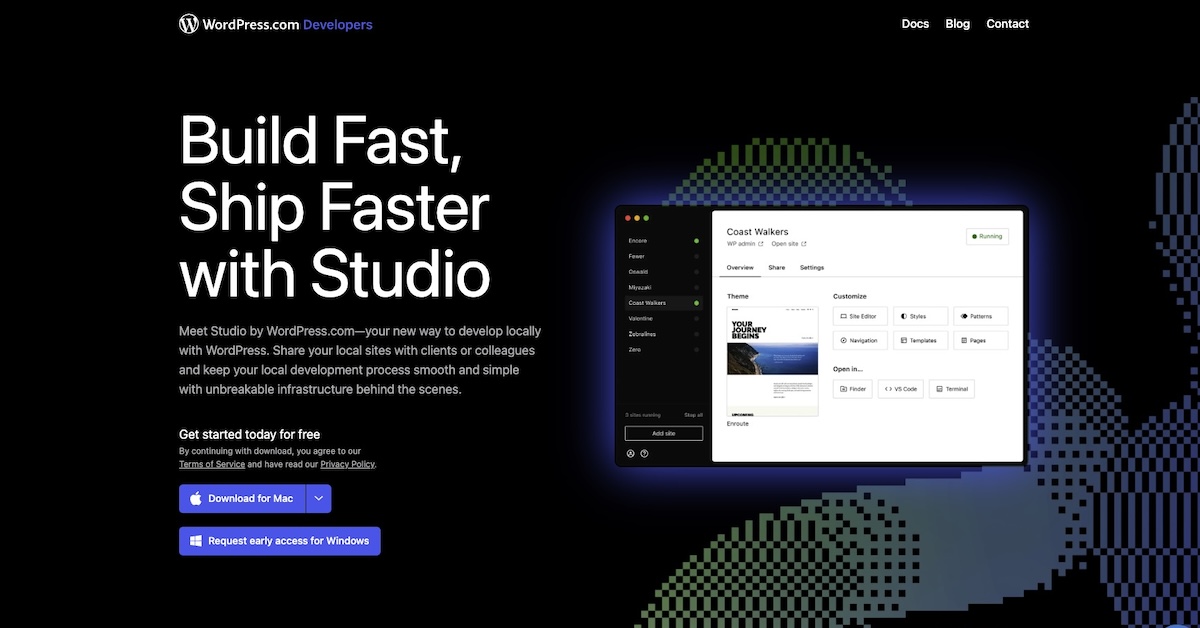
If you see this kind of pattern repeating in your Web server access log:
1.1.1.1 [30/May/2019:09:25:29 +0000] underattack.artisan.com.my "POST /wp-login.php HTTP/1.1" 403 2018 "-" "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:62.0) Gecko/20100101 Firefox/62.0"
1.1.1.1 [30/May/2019:09:25:31 +0000] underattack.artisan.com.my "GET /wp-login.php HTTP/1.1" 200 1669 "-" "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:62.0) Gecko/20100101 Firefox/62.0"
1.1.1.1 [30/May/2019:09:25:32 +0000] underattack.artisan.com.my "POST /wp-login.php HTTP/1.1" 200 2001 "-" "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:62.0) Gecko/20100101 Firefox/62.0"
2.2.2.2 [30/May/2019:09:30:16 +0000] underattack.artisan.com.my "POST /wp-login.php HTTP/1.1" 200 2001 "-" "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:62.0) Gecko/20100101 Firefox/62.0"
2.2.2.2 [30/May/2019:09:30:22 +0000] underattack.artisan.com.my "GET /wp-login.php HTTP/1.1" 200 1669 "-" "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:62.0) Gecko/20100101 Firefox/62.0"
2.2.2.2 [30/May/2019:09:30:28 +0000] underattack.artisan.com.my "POST /wp-login.php HTTP/1.1" 200 2001 "-" "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:62.0) Gecko/20100101 Firefox/62.0"
3.3.3.3 [30/May/2019:09:31:44 +0000] underattack.artisan.com.my "GET /wp-login.php HTTP/1.1" 200 1624 "-" "Mozilla/5.0 (Windows NT 6.1; WOW64; rv:40.0) Gecko/20100101 Firefox/40.1"
Most likely somebody is trying to login to your WordPress by bruteforcing the username and password.
Besides of the risk the attacker could gain access into your WordPress,
it could also bring down your WordPress site if the request are sent in huge amount like a DOS / DDOS attack,
since caching plugins won’t be caching wp-login.php, each request will hit to PHP itself and DB as well.
There’s two things we can do to mitigate the damage, and prevent further attack:
1. Install security plugins, like wp-cerber
– Enable some useful options such as ‘Block IP if login with Non-existing users’
– If you have a fixed IP, enable the option ‘Immediately block IP after any request to wp-login.php’, and put your fixed IP into whitelist
2. Use Cloudflare to help filtering out the malicious requests:
– Add a page rule in Cloudflare for URL *yourdomain.com/wp-login.php*
– Setting change Security Level -> I’m Under Attack
– Doing so would have minimal impact to users as they will be only going through the anti-ddos check when they login
Until now the attack to wp-login.php should be mitigated, there’s more hardening can be done for WordPress, but that’s a story for another day. 🙂